Introduction
Access Policy maps claim values to permissions, each time a user attempts to perform some administrator functionality their claims are evaluated against the policy to produce a set of permissions. Only if they have the appropriate permission will they be able to execute the functionality.
Managing your access policy
In order to manage your access policy, you will need to have the ‘All’ permission.
Access Policy Management is available in the Settings tab, new policies can be added and removed here. After making any changes you will need to save your changes in order for them to take effect.
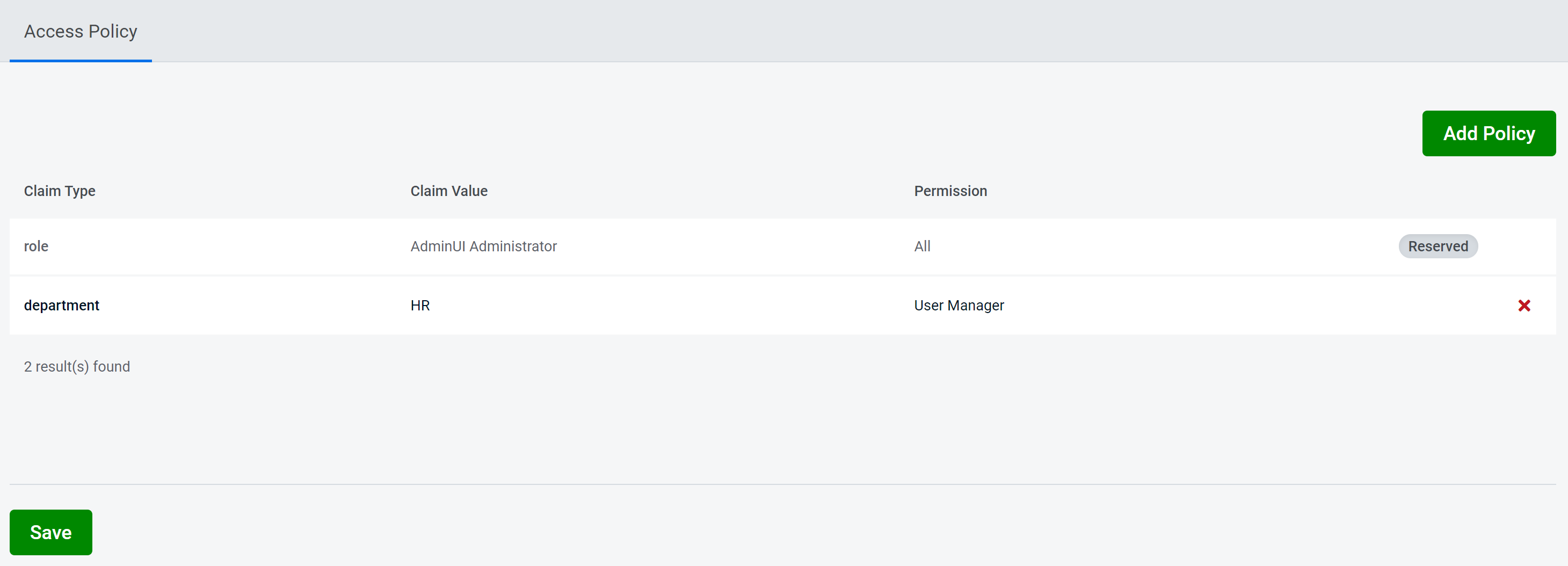
To make use of this new policy, you will need to give this new claim to a user. Users can get permissions from multiple access policy statements.
Only users with the ‘All’ permission are able to assign claims referenced in the access policy to themselves or other users.
Warning: any user that already has the claim in the access policy you are adding will be given the permission. This is also true if an access policy is removed, where any users with that claim will lose that permission.
Permissions
Users without any permissions will be greeted with an unauthorized screen after logging in.
Currently, there are three permissions available, each giving access to different actions within AdminUI:
User ManagerThis permission grants control over User and Role managementIdentity Server ManagerThis permission allows users to create and modify ClaimTypes, Clients, Identity Resources, and Protected ResourcesAllThis permission allows all of the above and control over Access Policy Management
By default, the 'AdminUI Administrator' role is set up by default with the All permission. This mapping cannot be removed.